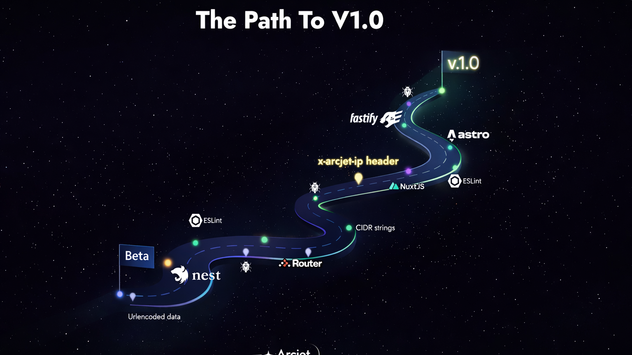
Arcjet JS SDK v1.0: Stability as a Developer Feature
We’ve just released v1.0 of the Arcjet JavaScript SDK. After more than two years of building, testing, and iterating in public, the
CEO of Arcjet (helping developers protect their apps). Co-Founder of Console (the best tools for developers). Researching sustainable computing at the University of Oxford.

We’ve just released v1.0 of the Arcjet JavaScript SDK. After more than two years of building, testing, and iterating in public, the
2025 was a defining year for Arcjet. We made deliberate progress across product, platform, and company, translating a clear focus into meaningful results. Over

The Arcjet Python SDK allows you to implement rate limiting, bot detection, email validation, and signup spam prevention in FastAPI and Flask style applications.

The tech stack behind Arcjet: WebAssembly runtimes, a Go gRPC decision API, and region-aware SNS→SQS→ClickHouse pipeline.
How Arcjet detects the real client IP in Firebase deployments, bypassing X-Forwarded-For issues by utilizing a custom Firebase header.

I recently joined James Governor at RedMonk to talk about why security tooling still feels years behind the rest of the developer ecosystem and
Get the full posts by email every week.